Introduction
Distributed Denial of Service (DDoS) attacks are among the most visible and disruptive cyber threats organizations face today. Unlike stealthy breaches that aim to steal data, DDoS attacks focus on overwhelming a service so legitimate users cannot access it. These incidents range from short-lived traffic spikes to prolonged campaigns that cripple websites, APIs, and online services for hours or days. For businesses and service providers, the consequences go beyond downtime lost revenue, damaged reputation, regulatory scrutiny, and expensive incident response can follow. This guide provides a practical, accurate overview of DDoS attacks, explains the technical mechanics in accessible terms, highlights the principal risks, and outlines actionable mitigation strategies. It’s written with an emphasis on clarity and trustworthiness: the recommendations reflect widely accepted industry practices and encourage consulting certified security professionals for implementation and compliance details.
What are DDoS attacks?
A Distributed Denial of Service (DDoS) attack is a coordinated attempt to make an online service unavailable by flooding it with traffic or exploiting weaknesses in network protocols. Instead of a single attacker and a single connection, a DDoS uses many compromised devices often forming a botnet to send a huge volume of traffic or malformed requests. The goal is to exhaust resources such as bandwidth, CPU, memory, or connection tables so legitimate user requests are dropped or delayed. DDoS attacks come in several flavors: volumetric attacks target bandwidth, protocol attacks exploit weaknesses in network stacks, and application-layer attacks target specific services like HTTP or DNS. While some attacks are blunt-force and easy to spot, others are stealthy and low-and-slow, blending with normal traffic to evade detection. Understanding the basic definition and motives from extortion and political activism to distraction for other intrusions is the first step toward building effective defenses.
How DDoS attacks work
At their core, DDoS attacks are about resource exhaustion. Attackers typically assemble or rent a network of compromised machines (botnet) to send coordinated traffic toward a target. Volumetric attacks saturate the target’s internet connection with large numbers of packets (UDP floods, amplification attacks), while protocol attacks aim to consume server or intermediary resources by exploiting protocol statefulness (SYN floods, TCP connection exhaustion). Application-layer attacks mimic legitimate user behavior to overload services that are expensive per request, such as complex search queries or login endpoints. Attackers may also combine tactics: a volumetric flood to distract and mask a targeted application-layer attack. Modern attacks often use reflection/amplification spoofed requests sent to open servers that reply to the victim increasing scale without revealing the attacker’s origin. Detection relies on traffic baselining, anomaly detection, and telemetry; mitigation often requires traffic filtering, rate limiting, and distributed scrubbing to separate malicious traffic from legitimate users.
Impact and risks of DDoS attacks
The immediate impact of a successful DDoS attack is service unavailability website outages, failed transactions, or broken APIs which directly hits revenue and user trust. Indirect effects include escalation of support costs, SLA breaches, and regulatory or contractual penalties. For online services that rely on real-time operations (e.g., fintech, gaming, e-commerce), the reputational damage can be severe and long-lasting. DDoS can also serve as a diversion, allowing attackers to carry out data breaches or ransomware during the chaos. From a technical standpoint, recovery expenses include increased bandwidth, mitigation service fees, forensic analysis, and infrastructure hardening. For small organizations without prepared defenses, even short attacks can cause outsized harm. Finally, DDoS incidents can expose weaknesses in incident response plans and vendor dependencies; companies without tested playbooks or communication strategies often respond slowly, compounding operational and legal risk.
Prevention and mitigation strategies
Mitigating DDoS requires layered defenses: preparation, detection, and response. Start with capacity planning and network redundancy distribute services across regions and providers where possible. Employ rate limiting and request validation at the edge to reduce the impact of application-layer attacks. Use a combination of on-premise DDoS appliances and cloud-based scrubbing/CDN services that can absorb volumetric floods and filter malicious traffic. Implement robust monitoring and baselining so anomalies trigger alerts early; integrate logs with SIEM for correlation. Use anycast routing and scalable load balancers to distribute traffic. For critical services, engage a managed DDoS protection vendor with a documented SLA and automated mitigation. Regularly test incident response plans with simulated DDoS scenarios and practice communication with stakeholders. Finally, ensure DNS resiliency (multiple providers, TTL planning) and review third-party vendor security dependencies are often exploited in attacks. Combining technical controls with planning, testing, and vendor relationships creates a resilient posture.
Conclusion
DDoS attacks remain a persistent and evolving threat that can cause immediate disruption and long-term damage. The good news is that many effective defenses are well established: layered architecture, traffic filtering, cloud scrubbing, monitoring, and practiced incident response dramatically reduce risk. Organizations should take a proactive approach assess exposure, implement baseline protections, engage reliable mitigation services for scale, and rehearse responses. Remember that a resilient strategy balances technical controls with clear communication and governance. If your service is critical or highly visible, consult certified cybersecurity professionals to tailor defenses and ensure compliance with applicable regulations. Preparedness and speed of response are the most valuable assets when facing DDoS build them before an attack arrives.
Frequently Asked Questions (FAQs)
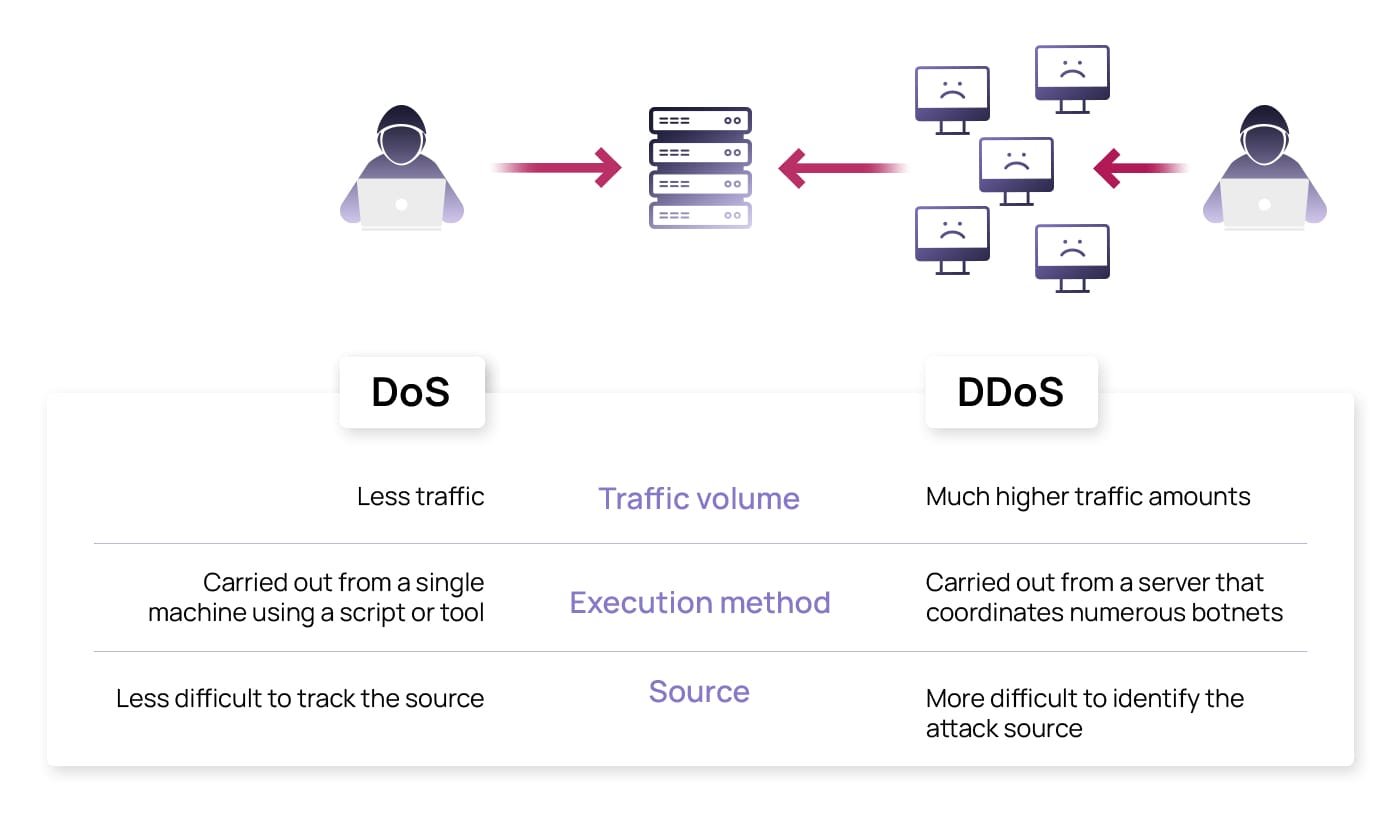
1. What’s the difference between DDoS and DoS?
A DoS (Denial of Service) attack originates from a single source to overwhelm a target, while a DDoS involves many distributed sources (botnet) acting together, making it larger in scale and harder to block.
2. Can small websites be targeted by DDoS?
Yes. Attackers often target small sites because they may lack mitigation resources; even modest attacks can make an under-provisioned site inaccessible.
3. How quickly should I respond to a DDoS?
Respond immediately: activate your incident plan, switch traffic to mitigation providers if configured, and communicate with stakeholders. Speed reduces downtime and limits cascading effects.
4. Are there legal remedies if my service is attacked?
Law enforcement can investigate large or traceable attacks, and some jurisdictions have cybercrime laws covering DDoS. Still, legal routes are slow; prioritize technical mitigation and preservation of logs for investigations.